This feature is avaliable in SP695+.
If you already have OpenVPN configured before the upgrade, you must create a new CA certificate and reconfigure the OpenVPN service and rebuild all the client scripts.
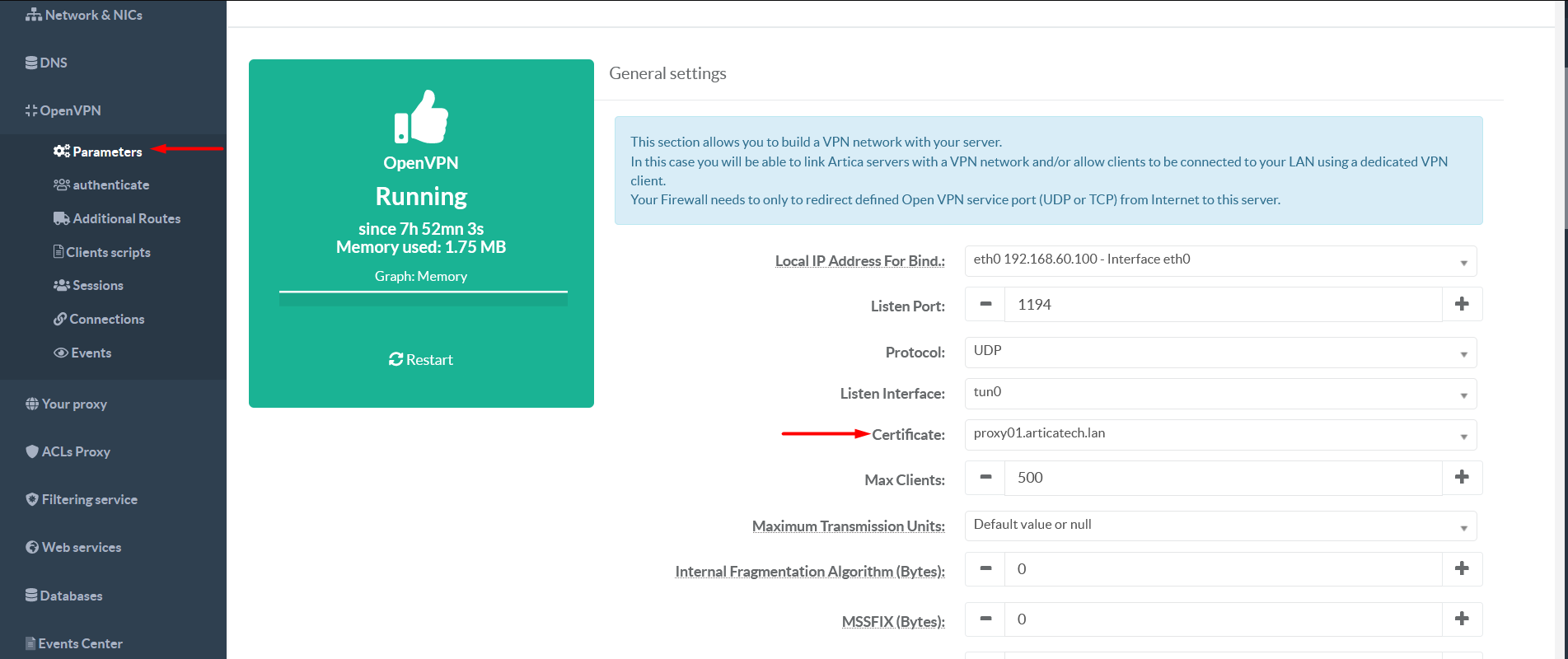
On left menu select OpenVPN
Parameters Select the new certificate to be used by the OpenVPN service
On the bottom of the page click Apply and then Reconfigure Service
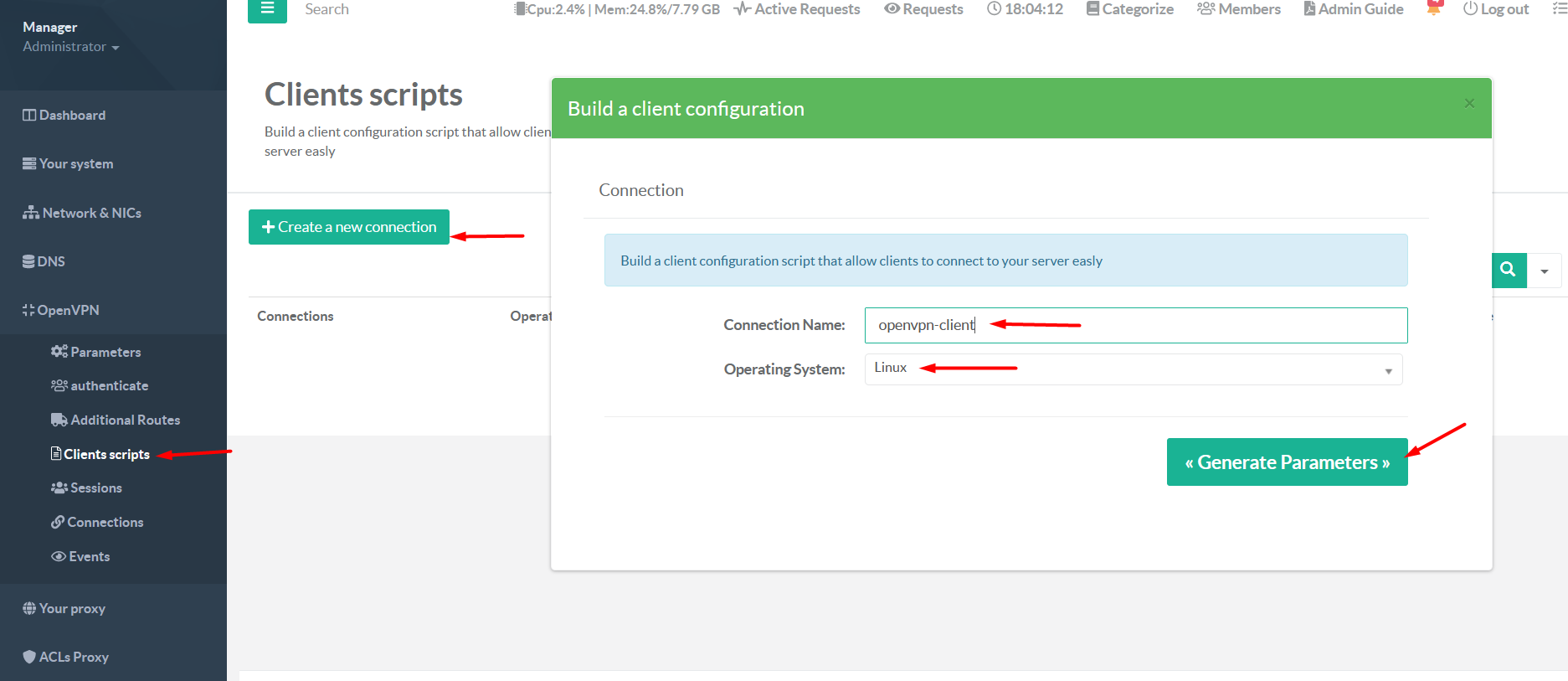
On left menu select OpenVPN
Client Scripts Click on the botton Create a new connection
Set the connection name
On operating system dropdown select Linux
Click on botton Generate parameters
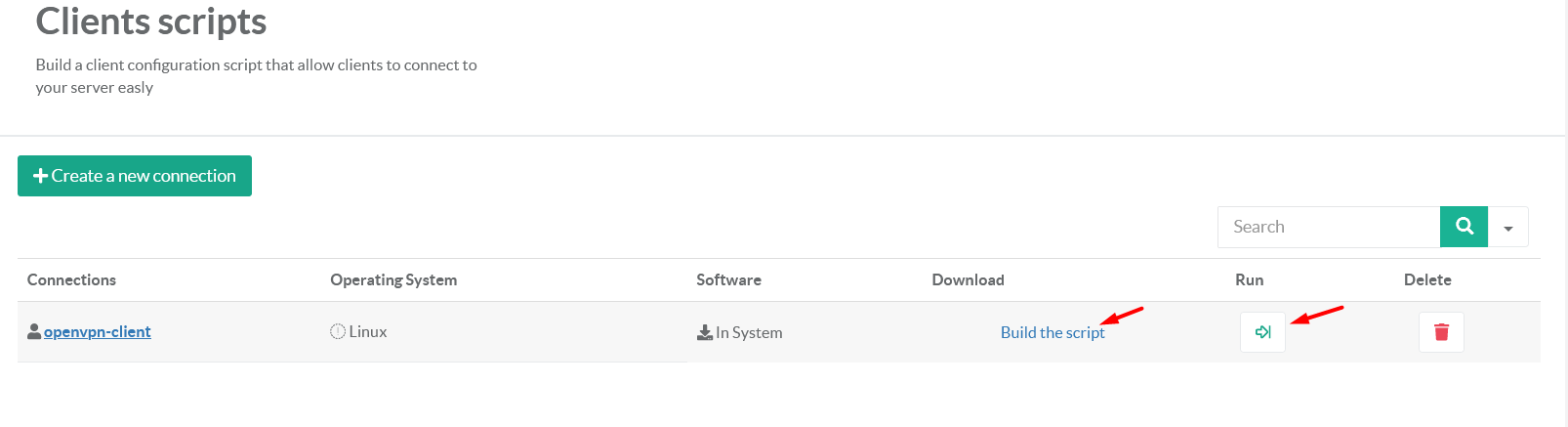
After you create the script, click on the button Build the script or Run
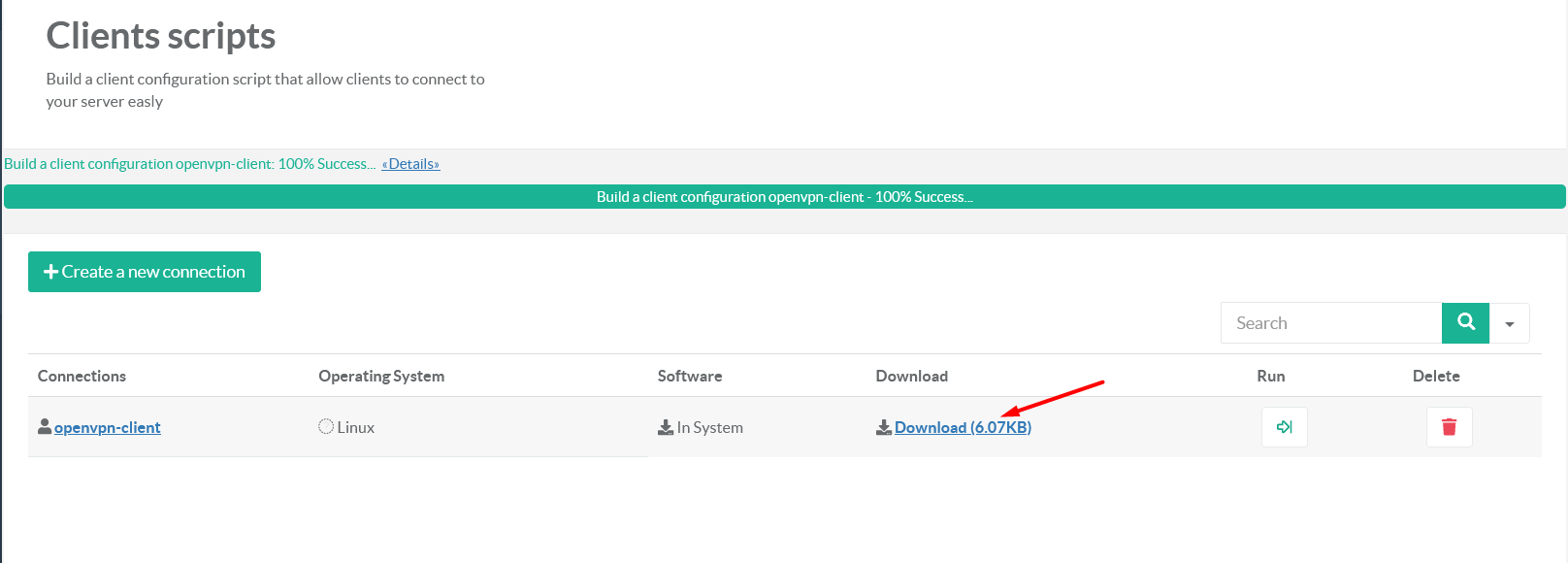
After you build the script, click on the button Download
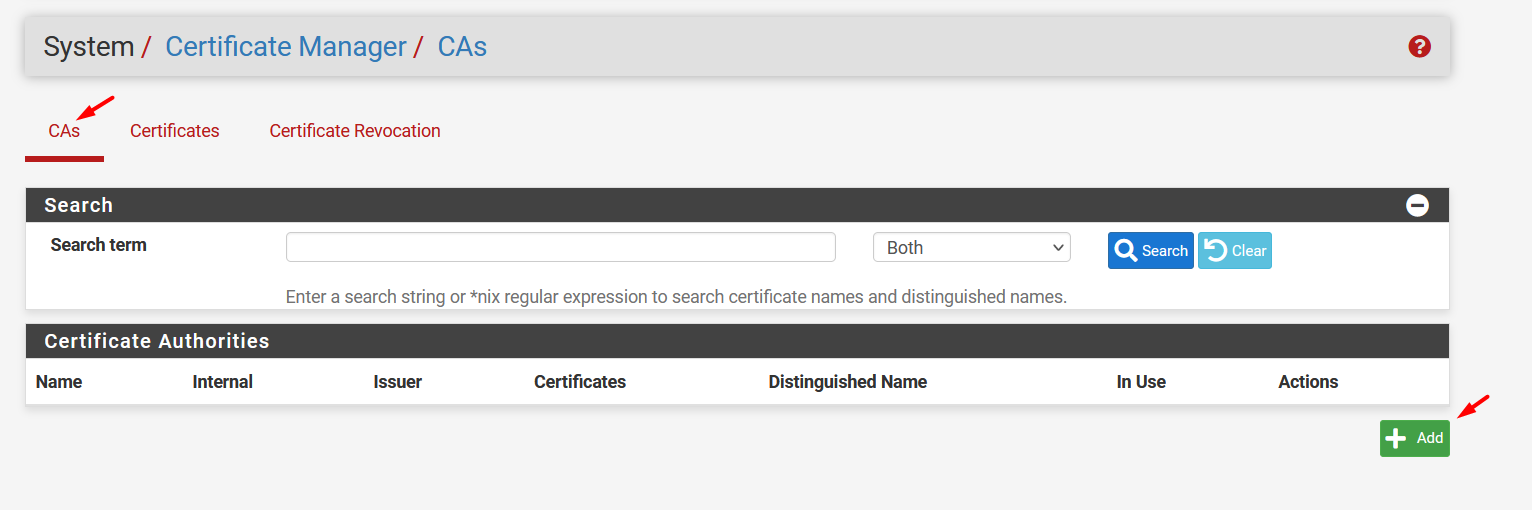
On pfSense, go to System / Certificate Manager
On CAs tab, click on the botton Add
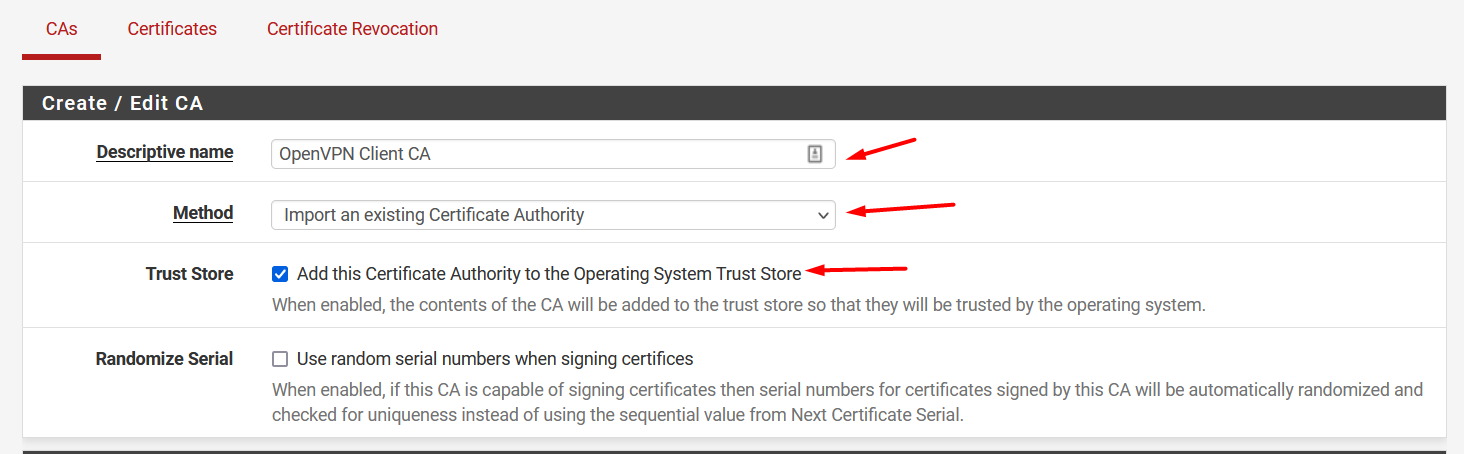
Set the Descriptive name
On Method dropdown, select Import an existing Certificate Authority
Check the option Trust Store
Open with notepad or other IDE the OpenVPN client script previously downloaded.
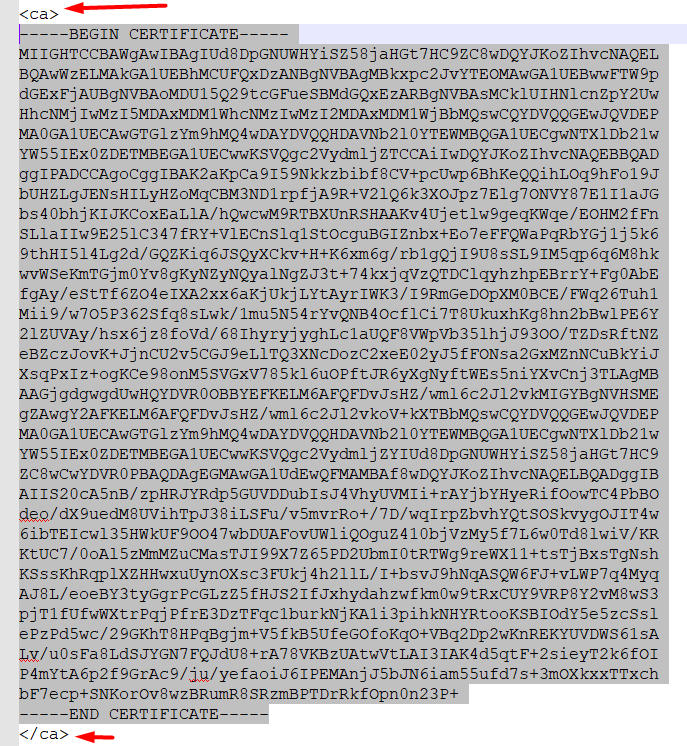
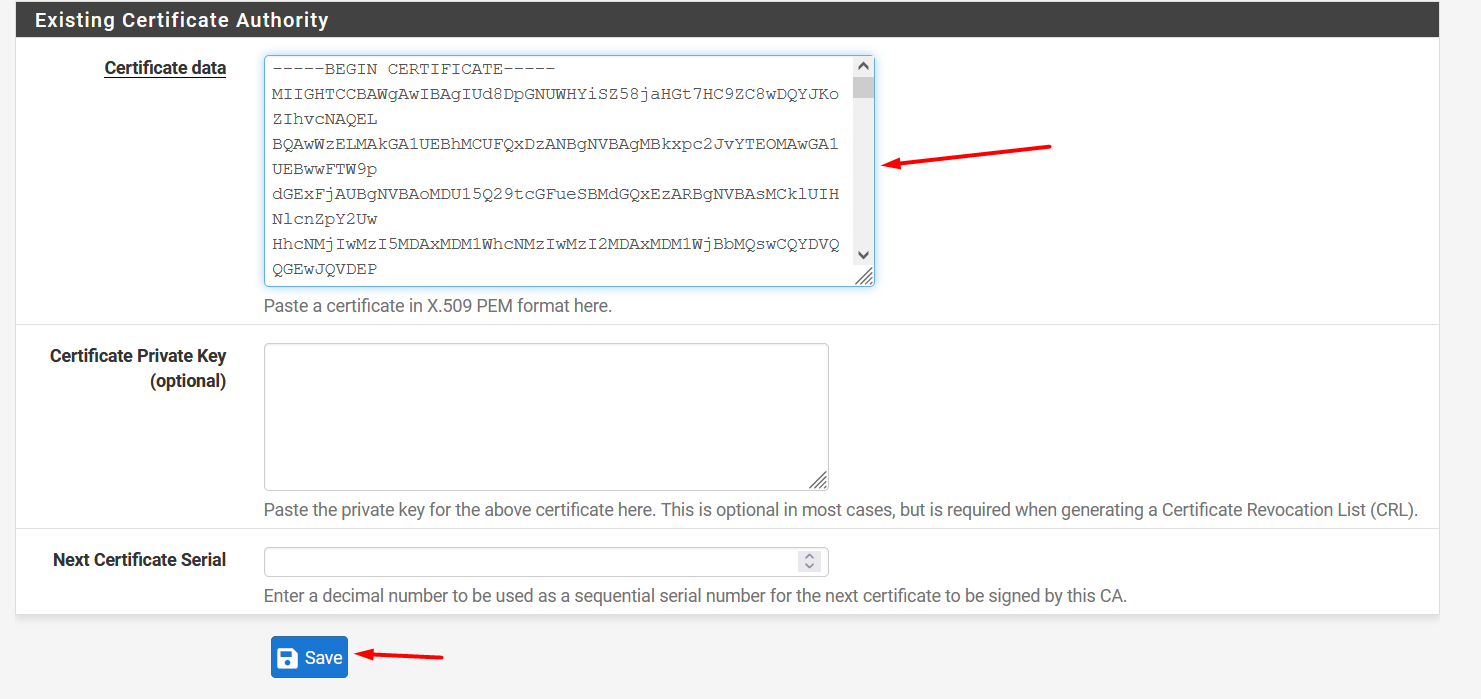
Copy the key inside < ca > tag and paste it inside Certificate data textarea.
Click Save
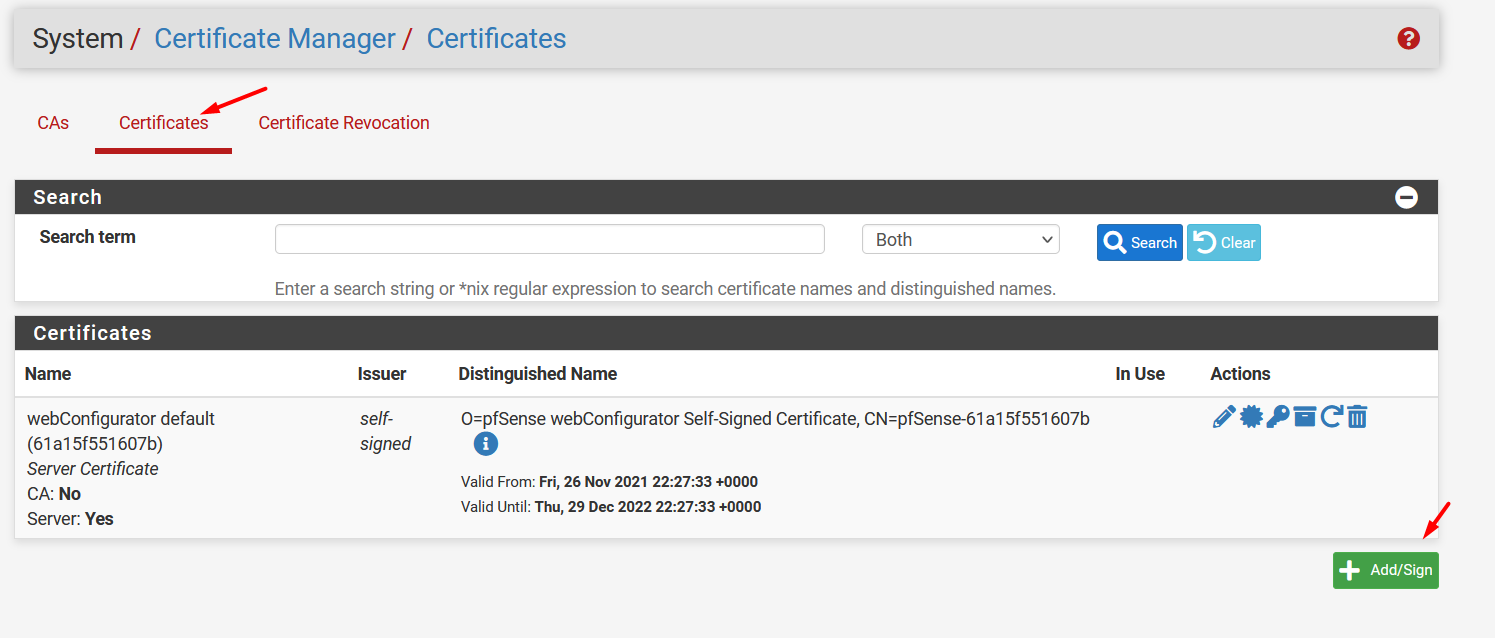
On pfSense, go to System / Certificate Manager
On Certificates tab, click on the botton Add/Sign
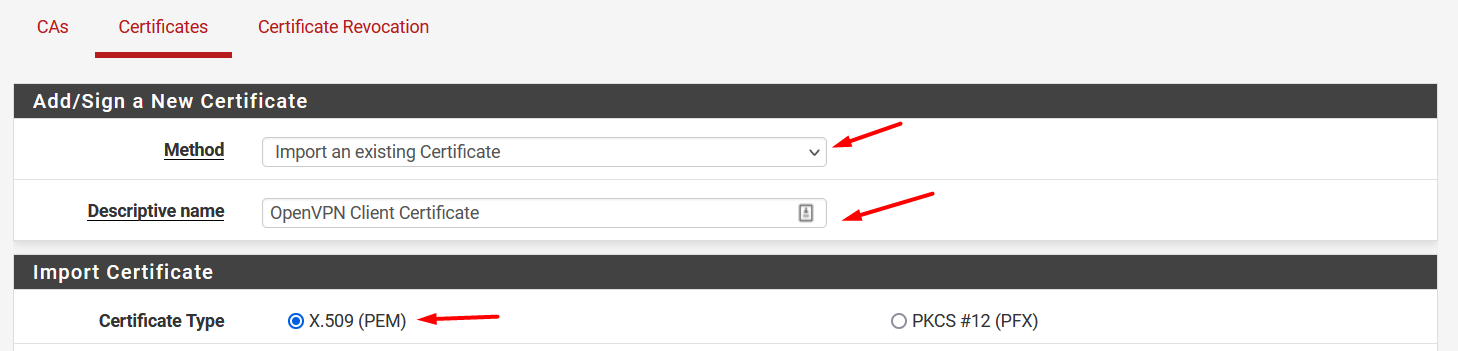
On Method dropdown, select Import an existing Certificate
Set the Descriptive name
In Certificate Type , select X.509 (PEM)
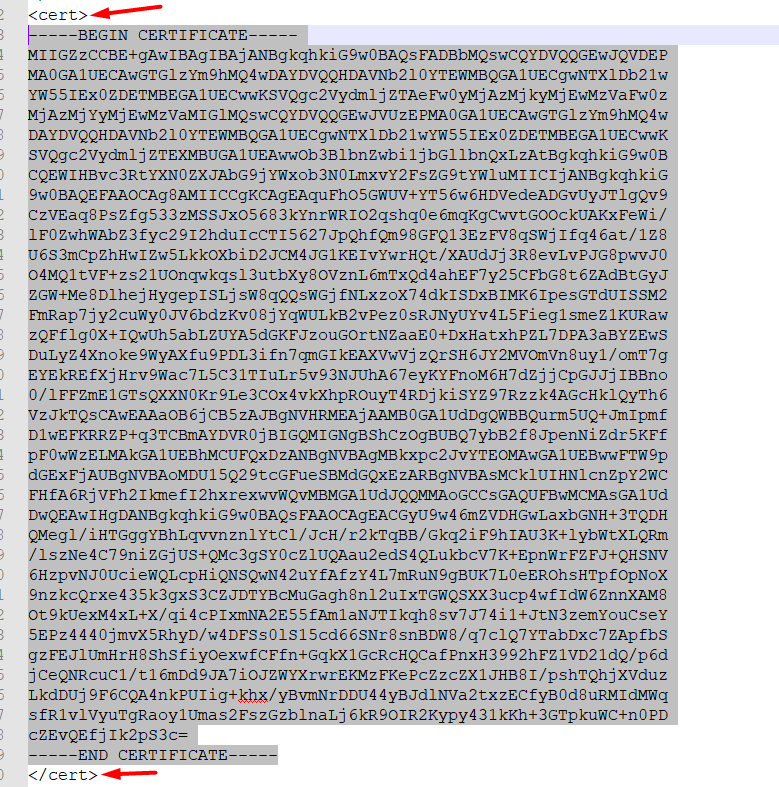
Open with notepad or other IDE the OpenVPN client script previously downloaded.
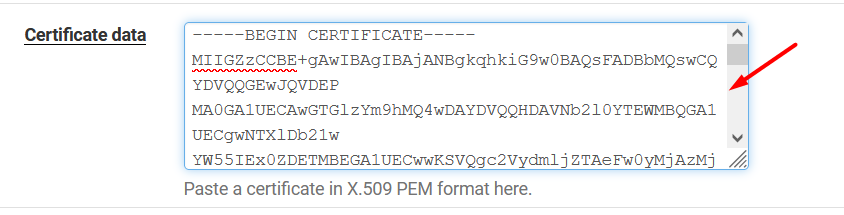
Copy the key inside < cert > tag and paste it inside Certificate data textarea.
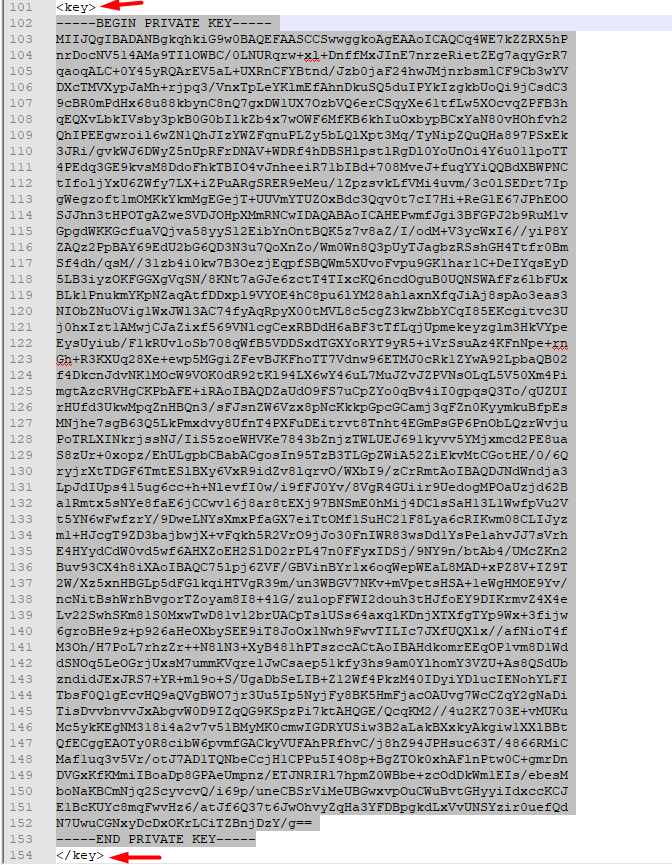
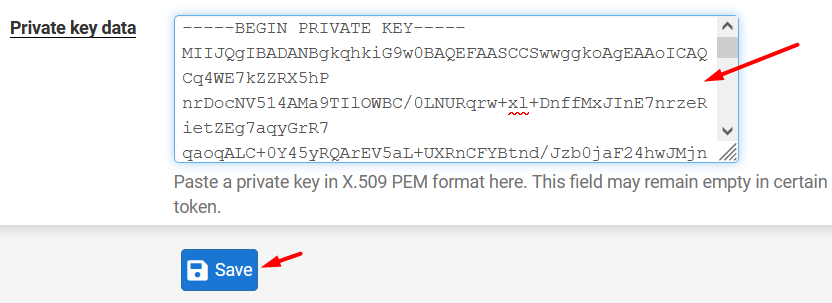
Copy the key inside < key > tag and paste it inside Private key data textarea.
Click Save
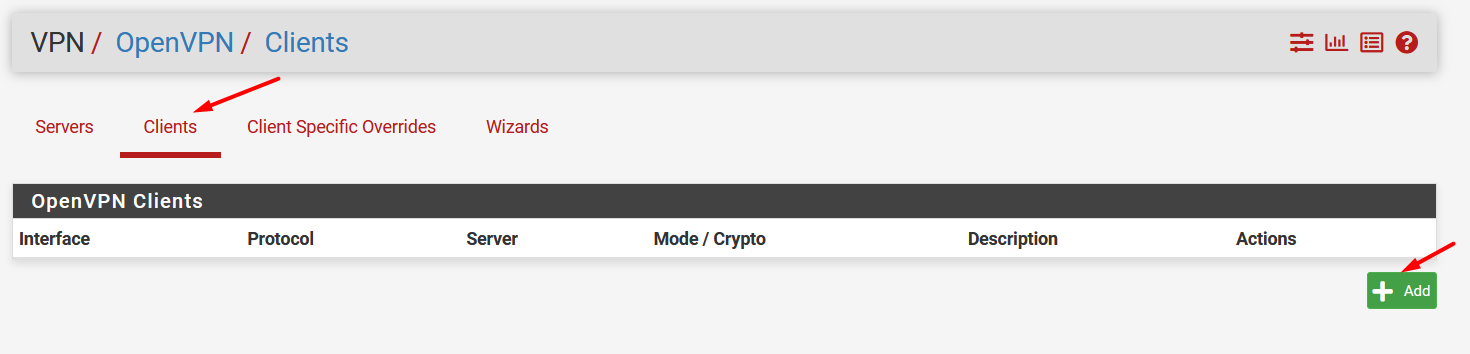
On pfSense, go to VPN / OpenVPN
Select Clients
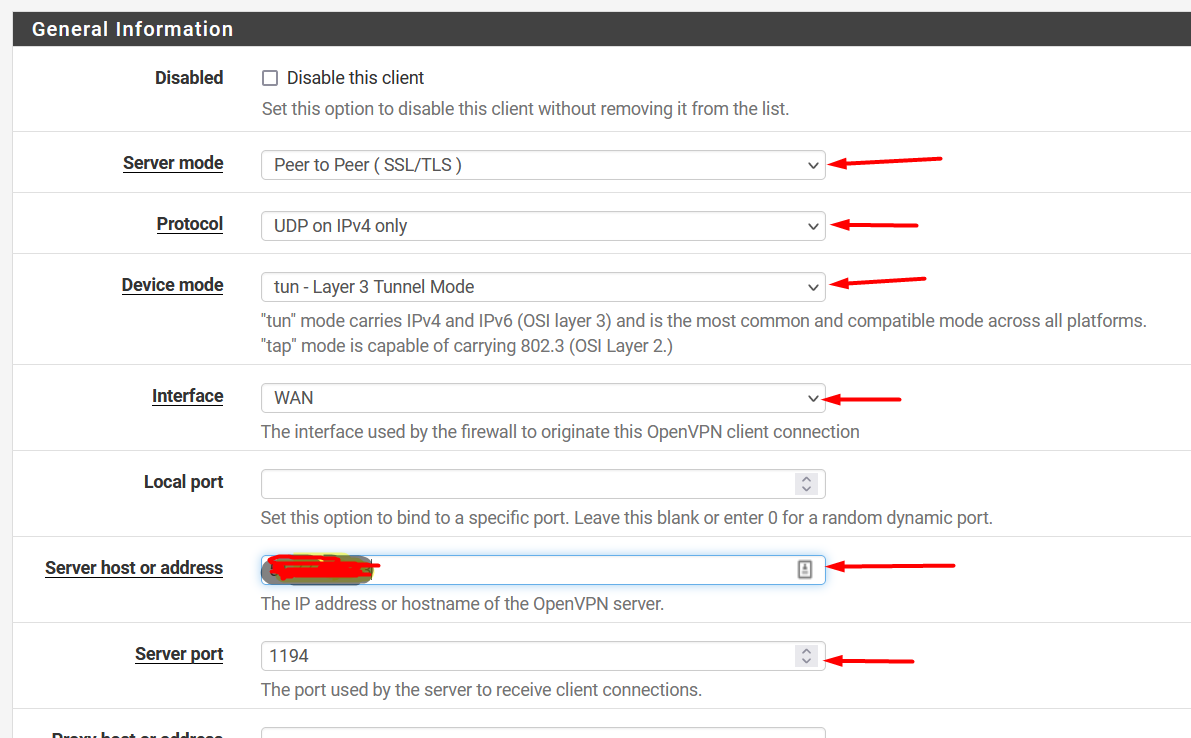
Add In Server Mode select Peer to Peer (TLS/SSL)
Set the Protocol configured on OpenVPN server, by default is UDP
Set the Device Mode configured on OpenVPN server, by default is Tun
Select the outgoing Interface to be used by the OpenVPN client.
Set the Server host or address of OpenVPN Server
Set the Server Port of OpenVPN Server
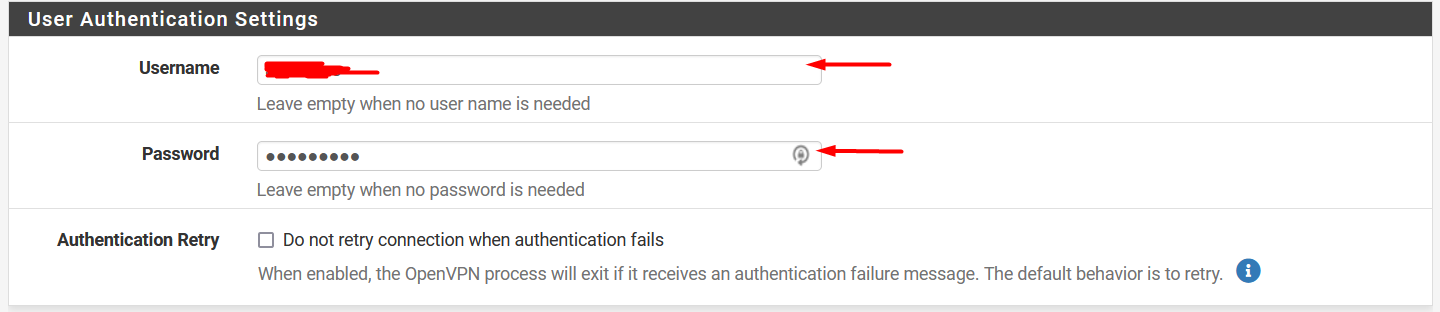
If you enable authentication on OpenVPN server, set the username and password
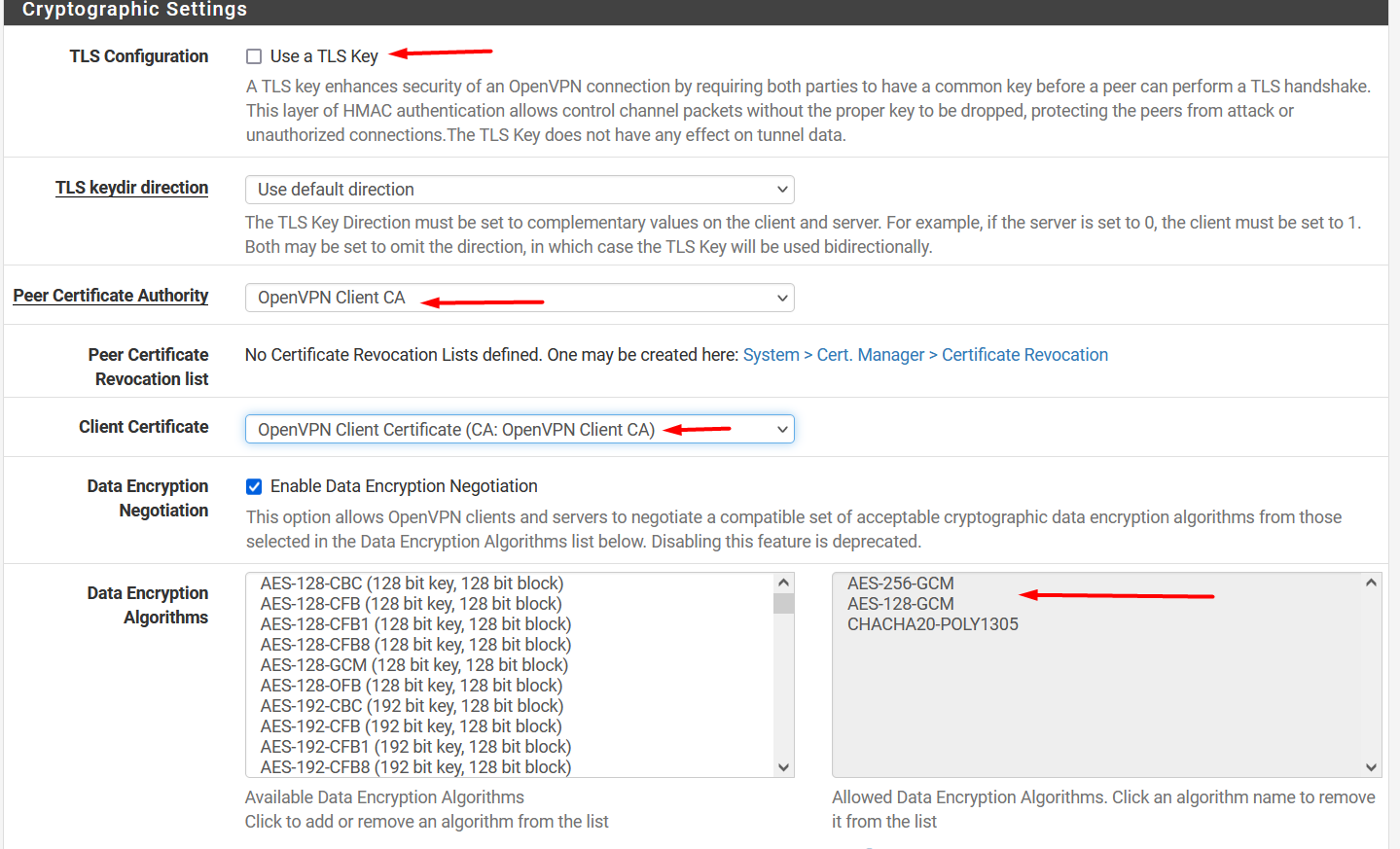
Uncheck the option Use a TLS Key
In Peer Certificate Authority select the CA certificate.
In Client Certificate select the client certificate.
Allow AES-256-GCM, AES-128-GCM and CHACHA20-POLY1307 in Data Encryption Algorithms
Save
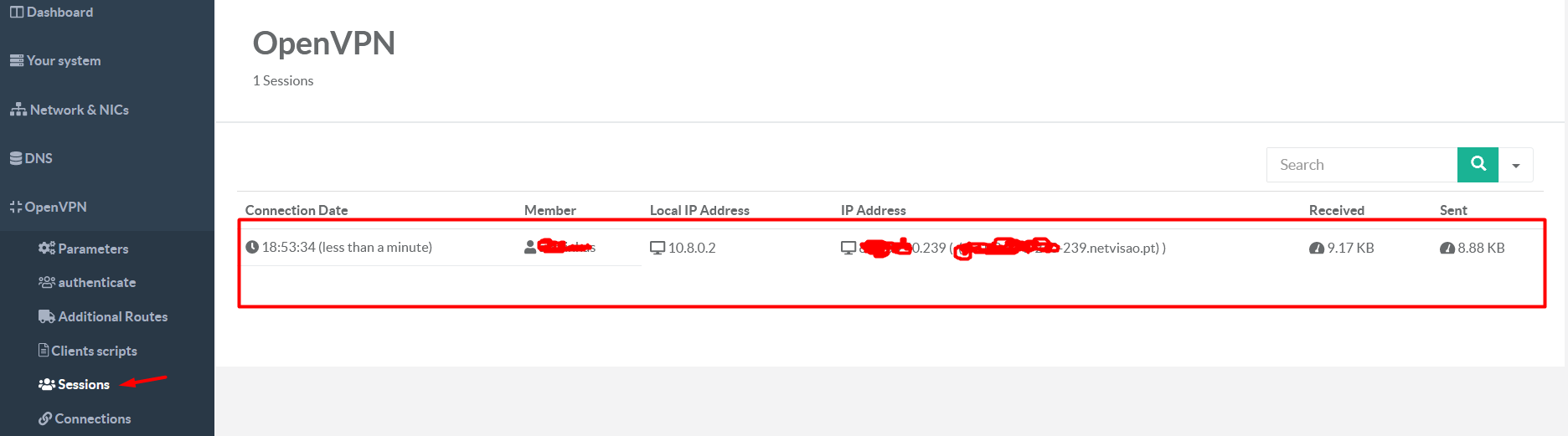
On left menu select OpenVPN
Sessions
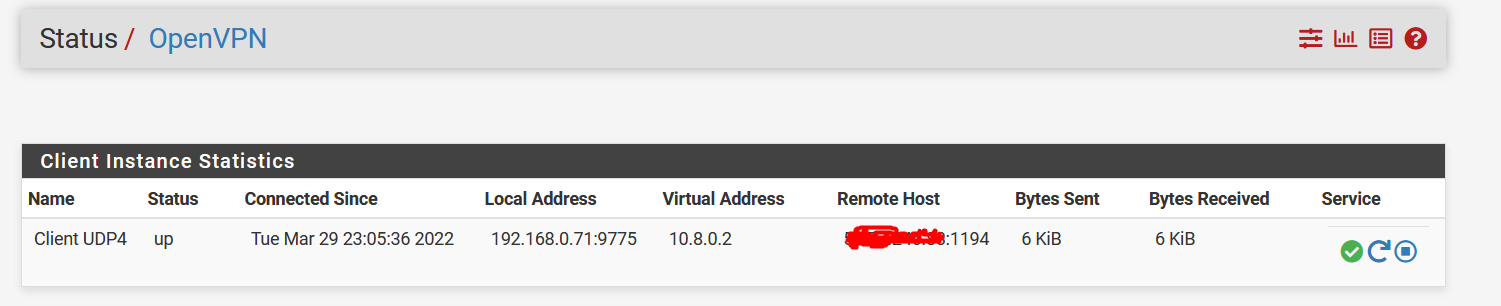
On menu Status , select OpenVPN